Blackhorse Perspectives: Success at the National Training Center – Security Operations
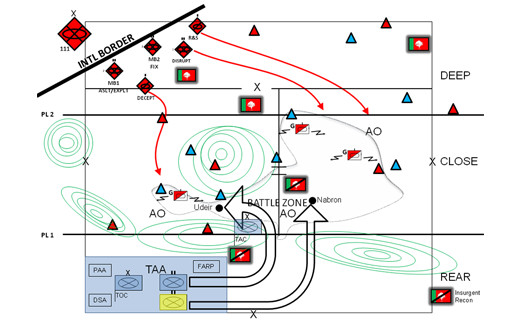
Figure 1. Blackhorse security operations.
(Editor’s note: This new column in ARMOR magazine is provided by 11th Armored Cavalry Regiment to inform maneuver units what the best practices for success are when deploying to the National Training Center for their rotations.)
The brigade tactical group (BTG) S-3 watched as the main effort executed a flawless forward-passage of lines through Siberia, then John Wayne Foothills, then breach at Whale Gap. He had a half-smile on his face, happy that the plan worked and the BTG was successful. He reflected on the successful zone reconnaissance the recon executed and how it contributed to the successful breach. He thought of many previous operations and how their result depended on security operations in both the offense and defense.
The 1st Squadron, 11th Armored Cavalry Regiment (ACR) conducted a review of security operations during decisive-action rotations in 2014 at the National Training Center (NTC) from three perspectives: conventional forces, guerrilla forces and paramilitary operations. The initial purpose of the review was to improve our core competencies and increase our lethality in preparation to train Brigade Combat Team (BCT) 2020 forces. BCT trends were observed, analyzed and discussed. It became apparent during this effort that the Blackhorse Regiment has a unique perspective and that we should strive to be good teammates to the force by sharing our analysis. In this particular review, 1/11 ACR focused on how security operations enable success at NTC. This article offers a way to execute security operations and provides more references for further study.
Successful security operations enable the decisive operation in several ways. They limit opposing-force (OPFOR) observations, limit OPFOR reporting and fires, and deny OPFOR key terrain. Units are successful if they plan, prepare and execute security operations using all elements and not relegate this function to the cavalry squadron and scout platoons. Security operations must be executed in the area of operations (AO) from start to finish of the operation to achieve a screen.
As defined in Army Doctrinal Reference Publication (ADRP) 3-90, security operations are “operations undertaken by a commander to provide early and accurate warning of enemy operations, to provide the force being protected with time and maneuver space.” The intent of security operations is to protect the front, flanks or rear of the friendly force, and ultimately afford commanders with the freedom to plan, resource and execute operations without enemy interdiction or surprise. Refer to ADRP 3-90 for details on the five security tasks of screen, guard, cover, area security and local security. This article narrows the scope to area and local security.
The scenario provided depicts the security challenges a BCT faces against the BTG (OPFOR) at NTC. Both units are executing a movement-to-contact in the area of NTC called Siberia near Mount Tiefort. One of the keys to success for the BCT in this scenario is execution of local security because it faces the additional challenge of a guerrilla presence in the AO.
Local security
Local security is defined as a relatively low-level but vital task intended to protect friendly positions from enemy actions on that position. Local security is required by all echelons and is a continuous effort to prevent enemy surprise and enemy reconnaissance from detecting the intent of friendly maneuver forces. Failure to conduct local security allows a guerrilla force freedom of movement through the unit’s security area. The guerrilla force executes reconnaissance operations – with as few as four individuals and two unmarked civilian vehicles – to provide timely and targetable compositions and dispositions to their higher headquarters. The result is execution of lethal action on high-value and high-payoff targets.
Successful units empower platoons and squads to execute local security as a continuous priority of work. This security task requires platoon- and company-level leadership enforcement of fundamental security measures, including the use of camouflage, noise and light discipline, employment of local observation posts, execution of local security patrols and standardized “stand-to” times integrated into a consolidated security plan. Also, all Soldiers require a basic knowledge of the operational environment (OE), which facilitates a broader understanding of the current threat picture and allows individual Soldiers to recognize potential security risks.
In this scenario, the BCT addresses local security through a clear statement of intent from the commander. The BCT commander directs the maneuver forces, enablers and supporting units to execute local security in their tactical assembly area (TAA). Each subordinate unit is responsible for executing patrols to deny guerrilla and special-operations forces the ability to conduct unrestricted area recon on the BCT TAA. The BCT assigns more local security forces from their maneuver units to secure critical assets necessary for mission success, such as position areas for artillery and Q36/37 radars. The BCT also plans to move its mission-command nodes and critical assets every 48-72 hours to make targeting difficult by reconnaissance assets.
Area security
Area security is defined in ADRP 3-90 as a “security task conducted to protect friendly forces, installations, routes and actions within a specific area.” Protected areas range from specific points within an AO such as intersections, to key terrain, routes or population areas.
Area security is another shaping operation that, when executed concurrently with decisive action, affords unit success against both conventional OPFOR and guerrilla forces. Successful units employ enablers (route clearance, military police, sustainers, engineers, etc.) augmented by combat units to execute this crucial shaping operation. These coordinated efforts focus security on population centers, restrictive terrain and the brigade support area to afford maneuver commanders with the time and space to conduct offensive or defensive operations, unimpeded by OPFOR.
A unit is most successful at NTC in the instances where it conducts aggressive area security with enabler units. In rotations during Fiscal Year 2014, the OPFOR could not deploy within population centers (urban terrain) by concealing both conventional anti-tank (AT) vehicles and non-conventional units equipped with AT weapons that could wait for the appropriate moment to maneuver on the unit flank and attack high-payoff targets. The OPFOR could not disrupt the training unit in depth and exploit a moment of weakness in the offense or defense.
In this scenario, the BCT secures population centers along its planned routes. Population centers were identified as objectives during the military decision-making process for the BCT to prevent OPFOR from hiding weapons systems and personnel from disrupting the BCT’s attack or lines of support during the operation. An entire population center does not have to be secure for the entire operation. The presence of the BCT within population centers before and during the movement-to-contact denies the OPFOR freedom of movement.
The 1/11 ACR determined through observation that units who execute security operations across the entire formation from start to finish of the mission are successful against the challenges imposed by the hybrid threat. Many potential adversaries use a hybrid threat – special operating forces working with an established insurgency or guerrilla force – to compensate for the technology gap with U.S. and allied forces. Improved integration between the conventional and unconventional threats makes successful security operations more imperative than ever for success in any OE.
The following two articles are recommended for study:
- CPT Hobson, Richard, and CPT Royle, Bradley, “Battalion Counter Reconnaissance, Flooding the Zone at the NTC,” Infantry magazine, January-February 1996, http://www.benning.army.mil/infantry/magazine/issues/1996/JAN-FEB/pdfs/JAN-FEB1996.pdf.
- MAJ Kranc, Ryan, “Cavalry Organizations and Task Terminology,” ARMOR, March-June 2014, /Armor/eArmor/content/issues/2014/MAR_JUN/Kranc.html.
 email
email print
print